 Are you smarter than a supermodel? Your data security and time will tell. (PHOTO: kateupton.com)
Are you smarter than a supermodel? Your data security and time will tell. (PHOTO: kateupton.com)Networks. Automation. Connectivity. The cloud. This isn’t your grandfather’s transportation system, or even your father’s. And if you’ve been in the business since before the turn of the millennium, it’s not even the world, technologically, that you made your first truck buck in.
The vehicles and highways may look much the same, but they’re not. As soon as 2020 – a scary, futuristic number for those of us of a certain age – you could very well be sharing the road daily with self-driving cars and trucks.
Robo-trucks are already feasible, of course, running commercially in closed loop operations and experimentally on the open Autobahn. But the idea of self-driving vehicles takes some getting used to: To see the guy in the driver’s seat of a truck reading a newspaper – okay, a tablet – as the rig rolls past is a tangible sign of significant change, and common sense says to go slow here. Let’s make sure it’s safe.
Yet virtually all of us now rely on satellites to tell us where to go, leave business decisions to algorithms we don’t understand and deposit our valuable assets and information with people we don’t know and in places that don’t exist.
The hacking of some celebrities’ personal photo streams has been big news this week, and it’s served as a good reminder to the general public of the risks of an online lifestyle.
For businesses, there’s more at stake than the embarrassment over an indiscretion made public, or the pain from a violation of personal privacy.
And, unlike photos of actresses, chances are good that serious intruders won’t be posting your sensitive business information on the internet for kicks – or at least not anywhere you’ll see it.
So, first, let’s take a look at some recent cyber-insecurity news that should be a heads-up for anyone in transportation and then we’ll ask around to find out what’s being done to protect us.
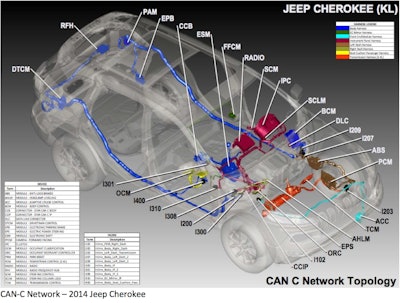 The 2014 Jeep has almost twice as many ECUs as the 2010, resulting in added complexity and new vulnerabilities.
The 2014 Jeep has almost twice as many ECUs as the 2010, resulting in added complexity and new vulnerabilities.Is your vehicle at risk? Noting the new passenger cars and trucks today have up to 100 electronic control units which do everything from tightening seatbelts to managing the throttle, brakes and steering – with most sharing data among themselves and a few communicating with the outside world – this study takes a look at 21 vehicles to assess potential risks for takeover. (For a technical view of the systems on a 2014 Ram 3500 and their potential vulnerabilities, see page 42.)
The authors – who last year had hacked into a Ford Escape and a Toyota Prius, taking control with a laptop plugged into a standard data port under the dash – discovered numerous potential holes, but conclude that getting a car’s computer systems to misbehave isn’t easy. They presented their research at last month’s Black Hat security conference in Las Vegas.
[youtube oqe6S6m73Zw nolink]
“If you have a vulnerability in your internet browser, someone may hack your computer and steal your credit card number,” author Chris Valasek tells Spectrum, the magazine of the Institute of Electrical and Electronics Engineers. “But if they hack into your car, while it seems it’s much more difficult, the circumstances could be them wrecking your car or tracking wherever you drive. So I think that’s why people tend to be a little more scared about it.”
The study does note, however, that a targeted attack is indeed possible – and worthwhile if the value is high enough.
On a related and somewhat lighter note, this presentation from DefCon 22 last month details a hacker’s exploration of his Volkswagen’s firmware, and discovers an array of possibilities with hidden media menus and company information. But the punch line is the hacker “bricked” his car, or made it inoperable. And it took three months to fix.
 Click to enlarge (Cesar Cerrudo graphic)
Click to enlarge (Cesar Cerrudo graphic)Does green mean go? Also at DefCon 22, a hacker demonstrated how to access common traffic control systems.
Essentially, Cesar Cerrudo explained, the systems are vulnerable because the sensors operate on insecure wireless technology.
Indeed, there re 50,000 such sensors that could be compromised, Cerrudo says, leading to traffic jams at intersections where stoplights would malfunction to accidents and gridlock.
The equipment value alone is $100 million. Add in the cost to replace or repair it, to say nothing of the lost productivity and accident toll, and sooner or later we’re talking real money.
Where am I? Of course, it was just a year ago that a team of students from the University of Texas created a device that transmitted false GPS signals, and in an experiment they managed to override legitimate GPS signals and gained control of the navigation of an $80 million yacht.
[youtube ctw9ECgJ8L0 nolink]
For mariners and pilots, that’s terrifying. For the coming of world of autonomous vehicles, it’s debilitating. For today’s hard working truck fleets: Don’t throw out the maps.
More broadly, Hewlitt-Packard last week published its Internet of Things State of the Union Study, revealing 70 percent of the most commonly used Internet of Things (IoT) devices contain serious vulnerabilities. IoT is a proposed development of the Internet in which everyday objects have network connectivity, allowing them to send and receive data.
In testing 10 such devices in use today, researchers found 90 percent collected at least one piece of personal data, either through the device itself, the cloud or an app. Additionally, 80 percent of the devices raised privacy concerns.
And guess what? All that connectivity can be severed with the flip of a switch. Again from a recent story in IEEE, “Electromagnetic Warfare Is Here,” this networked world “can be laid low by short, sharp pulses high in voltage but low in energy—output that can now be generated by a machine the size of a suitcase, batteries included.”
And these attacks aren’t just possible, they are happening, as the story explains.
What’s a person, or a business owner to do? Let’s discuss protections from all of the above in the next post.







